Lessons From Iowa: Secrecy Isn't Security
First, today’s tips.
Use two-factor authentication in life. If you get an e-mail from someone you know, and you’re not expecting it, use a second factor to check to make sure that the person it seems to come from actually sent it. Reporters do this now, and it’s a useful habit to develop. Iranian hackers are spear-phishing academics and others by pretending to be known journalists. Be mindful.
Twitter leans forward. Take time to read their new policies about synthetic and manipulated images. It has nuance but it also reflects clear-thinking. And remember: if someone spreads information about elections that can interfere with the integrity of the process, Twitter might ban the account. Of course, bad information will spread rapidly before Twitter can do its investigations, so this can’t be a panacea.
What can you say about Shadow’s app that the developer hasn’t already said?
One point: The Iowa Democrats did not want the developer’s identity known, they said, in order to prevent would-be intruders from trying to hack in to the software.
This was a huge mistake; open-source software is not unsecure software; as Zeynep Tufecki notes, often, because open-source software, developed, tested and iterated in public, is the safest and most secure software there is. Somehow, somewhere, someone, with good intentions, conflated secrecy with security, and that proved to be a catalyst for disaster. Point two:
“Anything developed this rapidly that has not been properly stress-tested—and is being used in the wild by thousands of people at the same time—is likely to crash the first time it is deployed.”
This was a known known. Why the Iowa Democrats did not anticipate this is a genuine question.
What I can say about the night of the caucuses: the Iowa Democratic Party either lacked or did not deploy a crisis communications plan, and they did not effectively counter disinformation or misinformation. A crisis comms plan would incorporate both the likeliest disaster (and this was foreseen) and allow for black swan catastrophes; it would force the party leaders to devote bandwidth during their scramble to collect and tabulate the votes to explain to people on all social/digital and legacy platforms what was happening, what wasn’t happening, and how they would communicate with the public going forward.
A few terse and defensive statements do not a crisis plan make. And this vacuum leaves room for people to create conspiracy theories out of whispers (It was a Pete put-up-job), all of which happen and rapidly spread.
Speaking of Charlie Kirk, a false claim he spread before Iowa about — FALSE CLAIM AHEAD — how the number of active voters in certain Iowa counties exceeded the number of people of voting age. FALSE CLAIM DONE. Judd Legum has a nice frame for how to combat that sort of misinformation. (It became disinformation quickly — 40,000 people retweeted the false claim!). Notice how Legum does NOT initially repeat the false claim. This is important.
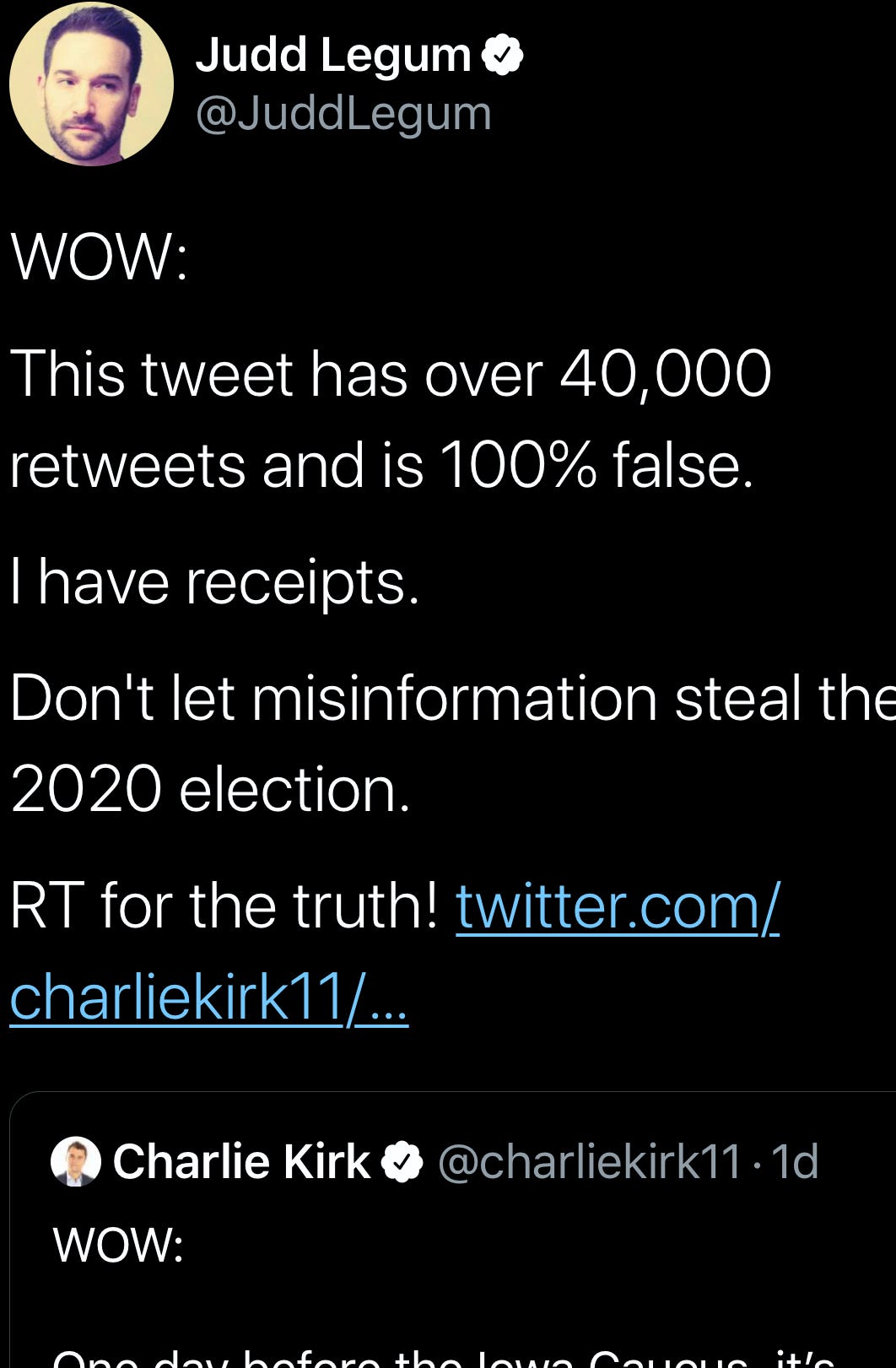
Disinformation paralyzes. Whatever residue of trust that people might have had in the caucus process has been scraped away by a royal flush of human error, technology problems, the social infrastructure that was built to exploit carnage, and malicious actors who know that the best way to own the other team is prevent the other team from even taking the field.


